This article will explain how to configure a Site-to-Site IPSec VPN using Cisco ASA 55XX’s using IKEV1. My example below shows how to configure VPN’s between 3 sites but can be modified for the following scenarios without much explanation:
- site-to-site VPN between 2 sites (Just remove SiteC… duh!)
- site-to-site to 3+ sites (just follow the example and modify for a N+1 sites. If You’re doing more than 3 sites, you may wish to look at a hub and spoke model to simply the network and backups, etc)
- Hub and spoke VPN, where 2 remote offices only connect to a main office (If SiteA is the Hub, on SiteB remove the SiteC configuration, on SiteC remove the SiteB configuration, etc…)
Overview
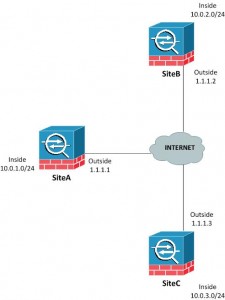
Network Diagram
Phase 1 Settings
| Attribute | Value |
|---|---|
| Authentication | Preshared Keys |
| Encryption | 3DES |
| Hash | MD5 |
| DH Group | Group 2 |
| Lifetime | 86400 seconds |
Phase 2 Settings
| Attribute | Value |
|---|---|
| Mode | Tunnel |
| Encryption | 3DES |
| Hash | SHA-1 |
| PFS | Enabled |
| Lifetime | 86400 seconds |
Configure SiteA
!----------------- !CONFIGURE OBJECTS !----------------- !Create Object for Local LAN SiteA config t object-group network obj-local network-object 10.0.1.0 255.255.255.0 end !Create Object for Remote LAN SiteB config t object-group network obj-SiteB network-object 10.0.2.0 255.255.255.0 end !Create Object for Remote LAN SiteC config t object-group network obj-SiteC network-object 10.0.3.0 255.255.255.0 end ! !--------------- !CONFIGURE ACL's !--------------- !Configure VPN ACL SiteB config t access-list ACL_SiteB extended permit ip object-group obj-local object-group obj-SiteB end !Configure VPN ACL SiteC config t access-list ACL_SiteC extended permit ip object-group obj-local object-group obj-SiteC end ! !------------------------ !CONFIGURE NAT EXEMPTIONS !------------------------ !Configure NAT Exemption SiteB config t nat (inside,outside) 1 source static obj-local obj-local destination static obj-SiteB obj-SiteB no-proxy-arp route-lookup end !Configure NAT Exemption SiteC config t nat (inside,outside) 1 source static obj-local obj-local destination static obj-SiteC obj-SiteC no-proxy-arp route-lookup end ! !----------------------------------------------------- !CONFIGURE PHASE1 PROPOSAL (pre-g2-3des-md5 SA:84600s) !----------------------------------------------------- config t crypto ikev1 policy 10 authentication pre-share encryption 3des hash md5 group 2 lifetime 86400 crypto ikev1 enable outside end ! !------------------------------------------------------------------- !CONFIGURE PHASE 2 PROPOSALS !------------------------------------------------------------------- !Configure Transform Set(g2-esp-3des-sha SA:84600s PFS:enabled) config t crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac end !Configure Transform Set (g2-esp-3des-md5 SA:84600s PFS:enabled) config t crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac end !Configure Tunnel Group Remote WAN IP SiteB(Replace VPNSHAREDKEYPW) config t tunnel-group 1.1.1.2 type ipsec-l2l tunnel-group 1.1.1.2 ipsec-attributes pre-shared-key VPNSHAREDKEYPW end !Configure Tunnel Group Remote WAN IP SiteC(Replace VPNSHAREDKEYPW) config t tunnel-group 1.1.1.3 type ipsec-l2l tunnel-group 1.1.1.3 ipsec-attributes pre-shared-key VPNSHAREDKEYPW end !Configure Crypto Maps (You can only have 1 crypto map nam and each VPN needs an unique Map # to differentiate from each other) !MAP: SiteA=1, SiteB=2, SiteC=3 config t crypto map crypto-map 2 match address ACL_SiteB crypto map crypto-map 2 set peer 1.1.1.2 crypto map crypto-map 2 set transform-set ESP-3DES-SHA end config t crypto map crypto-map 3 match address ACL_SiteC crypto map crypto-map 3 set peer 1.1.1.3 crypto map crypto-map 3 set transform-set ESP-3DES-SHA end !Attach Crypto Map to Interface config t crypto map crypto-map interface outside end
Configure SiteB
!----------------- !CONFIGURE OBJECTS !----------------- !Create Object for Local LAN SiteB config t object-group network obj-local network-object 10.0.2.0 255.255.255.0 end !Create Object for Remote LAN SiteA config t object-group network obj-SiteA network-object 10.0.1.0 255.255.255.0 end !Create Object for Remote LAN SiteC config t object-group network obj-SiteC network-object 10.0.3.0 255.255.255.0 end ! !--------------- !CONFIGURE ACL's !--------------- !Configure VPN ACL SiteA config t access-list ACL_SiteA extended permit ip object-group obj-local object-group obj-SiteA end !Configure VPN ACL SiteC config t access-list ACL_SiteC extended permit ip object-group obj-local object-group obj-SiteC end ! !------------------------ !CONFIGURE NAT EXEMPTIONS !------------------------ !Configure NAT Exemption SiteA config t nat (inside,outside) 1 source static obj-local obj-local destination static obj-SiteA obj-SiteA no-proxy-arp route-lookup end !Configure NAT Exemption SiteC config t nat (inside,outside) 1 source static obj-local obj-local destination static obj-SiteC obj-SiteC no-proxy-arp route-lookup end ! !----------------------------------------------------- !CONFIGURE PHASE1 PROPOSAL (pre-g2-3des-md5 SA:84600s) !----------------------------------------------------- config t crypto ikev1 policy 10 authentication pre-share encryption 3des hash md5 group 2 lifetime 86400 crypto ikev1 enable outside end ! !------------------------------------------------------------------- !CONFIGURE PHASE 2 PROPOSALS !------------------------------------------------------------------- !Configure Transform Set(g2-esp-3des-sha SA:84600s PFS:enabled) config t crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac end !Configure Transform Set (g2-esp-3des-md5 SA:84600s PFS:enabled) config t crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac end !Configure Tunnel Group Remote WAN IP SiteA(Replace VPNSHAREDKEYPW) config t tunnel-group 1.1.1.1 type ipsec-l2l tunnel-group 1.1.1.1 ipsec-attributes pre-shared-key VPNSHAREDKEYPW end !Configure Tunnel Group Remote WAN IP SiteC(Replace VPNSHAREDKEYPW) config t tunnel-group 1.1.1.3 type ipsec-l2l tunnel-group 1.1.1.3 ipsec-attributes pre-shared-key VPNSHAREDKEYPW end !Configure Crypto Maps (You can only have 1 crypto map nam and each VPN needs an unique Map # to differentiate from each other) !MAP: SiteA=1, SiteB=2, SiteC=3 config t crypto map crypto-map 1 match address ACL_SiteA crypto map crypto-map 1 set peer 1.1.1.1 crypto map crypto-map 1 set transform-set ESP-3DES-SHA end config t crypto map crypto-map 3 match address ACL_SiteC crypto map crypto-map 3 set peer 1.1.1.3 crypto map crypto-map 3 set transform-set ESP-3DES-SHA end !Attach Crypto Map to Interface config t crypto map crypto-map interface outside end
Configure SiteC
!----------------- !CONFIGURE OBJECTS !----------------- !Create Object for Local LAN SiteC config t object-group network obj-local network-object 10.0.3.0 255.255.255.0 end !Create Object for Remote LAN SiteA config t object-group network obj-SiteA network-object 10.0.1.0 255.255.255.0 end !Create Object for Remote LAN SiteB config t object-group network obj-SiteB network-object 10.0.2.0 255.255.255.0 end ! !--------------- !CONFIGURE ACL's !--------------- !Configure VPN ACL SiteA config t access-list ACL_SiteA extended permit ip object-group obj-local object-group obj-SiteA end !Configure VPN ACL SiteB config t access-list ACL_SiteB extended permit ip object-group obj-local object-group obj-SiteB end ! !------------------------ !CONFIGURE NAT EXEMPTIONS !------------------------ !Configure NAT Exemption SiteA config t nat (inside,outside) 1 source static obj-local obj-local destination static obj-SiteA obj-SiteA no-proxy-arp route-lookup end !Configure NAT Exemption SiteB config t nat (inside,outside) 1 source static obj-local obj-local destination static obj-SiteB obj-SiteB no-proxy-arp route-lookup end ! !----------------------------------------------------- !CONFIGURE PHASE1 PROPOSAL (pre-g2-3des-md5 SA:84600s) !----------------------------------------------------- config t crypto ikev1 policy 10 authentication pre-share encryption 3des hash md5 group 2 lifetime 86400 crypto ikev1 enable outside end ! !------------------------------------------------------------------- !CONFIGURE PHASE 2 PROPOSALS !------------------------------------------------------------------- !Configure Transform Set(g2-esp-3des-sha SA:84600s PFS:enabled) config t crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac end !Configure Transform Set (g2-esp-3des-md5 SA:84600s PFS:enabled) config t crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac end !Configure Tunnel Group Remote WAN IP SiteA(Replace VPNSHAREDKEYPW) config t tunnel-group 1.1.1.1 type ipsec-l2l tunnel-group 1.1.1.1 ipsec-attributes pre-shared-key VPNSHAREDKEYPW end !Configure Tunnel Group Remote WAN IP SiteB(Replace VPNSHAREDKEYPW) config t tunnel-group 1.1.1.2 type ipsec-l2l tunnel-group 1.1.1.2 ipsec-attributes pre-shared-key VPNSHAREDKEYPW end !Configure Crypto Maps (You can only have 1 crypto map nam and each VPN needs an unique Map # to differentiate from each other) !MAP: SiteA=1, SiteB=2, SiteC=3 config t crypto map crypto-map 1 match address ACL_SiteA crypto map crypto-map 1 set peer 1.1.1.1 crypto map crypto-map 1 set transform-set ESP-3DES-SHA end config t crypto map crypto-map 2 match address ACL_SiteB crypto map crypto-map 2 set peer 1.1.1.2 crypto map crypto-map 2 set transform-set ESP-3DES-SHA end !Attach Crypto Map to Interface config t crypto map crypto-map interface outside end
Further Info
I would suggest using IKEV2 for a Site-to-Site VPN, and I’ll outline the steps a in future article once I get time to write it up…. Stay tuned!

3 comments
Awesome article!
Im running into a particular situation. I have a cisco ASA-x for a branch. the firewalls is at the perimeter with NAT_PAT configured for the DMZ and internal users to connect out on the OUTSIDE interface as DHCP. Also NAT port forwarding for the DMZ servers.
Im trying to do a l2l Ipsec tunnel. Traffic is being allowed by IP from the remote host and IPsec enabled… everything is configured but nothing comes. Im suspecting is the remote user not having ESP enabled on their WAN to allow the communication. My question on my end do i need to do a NAT except since traffic or the tunnel will be terminated on the OUTSIDE interface? I mean the interesting traffic would need to do a NAT except? such as NAT (OUTSIDE,ANY) static remote_subnet destination subnet remote_subnet destination_subnet ?
I’ve done many IPsec tunnels where we have a router passing the traffic thru to the VPN concentrator but never when it terminates right at the WAN side.
Hi,
Do you have an example configuration for ASA full mesh VPN?
Sorry, I don’t have any live examples to pull this from but may put some up once I get time to play with them in my lab!